The Internet-Wide Scans Data Repository (scans.io) was created alongside Censys. The purpose of this repository is to provide raw datasets that were gathered during periodic Internet-wide scans by Censys. How is this useful in cybersecurity?
- You can download the dataset and start doing lookups and statistics which wouldn’t be possible using Censys Web UI or REST API.
- The repository is not limited to data from Censys. Other organizations and researchers can upload the results of their own researches.
It is the latter point that this post will focus on. I provide technical details and practical use cases (mainly for reconnaissance).
Rapid7 runs their own Internet-wide research called Project Sonar. Often forgotten fact is, that data from Project Sonar is not included in Censys Web UI results.
DNS
Let’s first discuss how DNS is scanned on the Internet-wide level. If you are not interested in such technical details, feel free to skip directly to Usecases.
Censys uses port scan on port 53. It detects DNS servers and resolvers around the globe. Censys also does some form of “health check”. It tries to resolve A record for the specific domain name (c.afekv.com) to see, whether DNS resolver returns the correct value. This method can reveal rogue public DNS resolvers around the globe. This is an example of a result that Censys provides for 8.8.8.8. If you are interested in researching open DNS resolvers, I recommend checking public-dns.info.
There is, however, another side of DNS scanning. While Censys takes scanning approach which operates on the transport layer (L4), Project Sonar uses application layer (L7) for DNS scanning. In other words, Project Sonar provides the dataset which contains domain names and their corresponding resource record values gathered at some point in time. This creates entirely new visibility into DNS from the global perspective. We can cluster domain names which resolve to the same IP address, look for DGAs, see most popular mail server providers, and much more.
How can Project Sonar achieve this?
Forward DNS study (Rapid7 link)
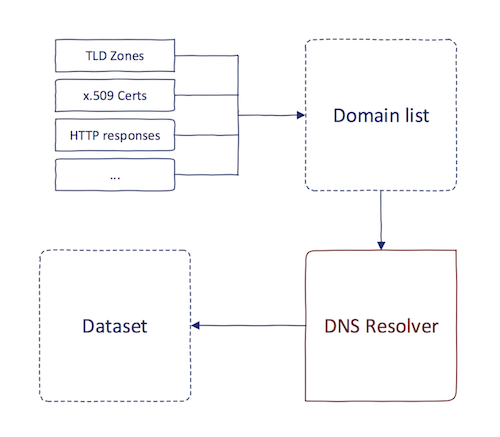
Project Sonar starts by collecting a large number of possible domain names (even non-existing ones). This is an essential step because we cannot query IP address to give us all domain names pointing to it. DNS just doesn’t work this way. Sources of these domain names include:
- Dumps of TLD zone files (.com, .net, ccTLDs, …)
- Domains found in responses from HTTP study
- CN and SubjectAltName fields in x.509 certificates from SSL study
While documentation doesn’t provide a full list of sources, there is a good chance that third party threat intel sources are used for gathering additional domain names. Note that this list doesn’t only include second-level domain names, but also subdomains and higher-level domain names (or FQDN). On the other hand, the list is by no means complete. There is no way we can find every possible FQDN on the Internet.
Once the list of all potential domain names is gathered, the resolution part starts. The resolution takes a domain name and queries its DNS server to get record values such as a, mx, soa, …
Now, here it gets a little complex. To decrease network traffic, Project Sonar uses ANY “meta-query” type to get all possible record values at once. ANY tells DNS server: “Give me every record you have for this domain name”. Unfortunately, ANY query also increases the load on DNS servers and providers such as CloudFlare stopped responding to ANY queries. Alternatively to ANY query, iterative DNS resolution can be used. This resolution queries each record type one-by-one (e.g., first A record, then AAAA, then MX, ...). Project Sonar is slowly moving towards this resolution as explained further below.
After the resolution phase, the final dataset is produced. It is a GZ-compressed file having ~23GB. Its structure is pretty straightforward:
- Text file having one entry per line
- Each entry is separate JSON
...
{"timestamp":"1506765777","name":"example.com","type":"a","value":"93.184.216.34"}
{"timestamp":"1506765777","name":"example.com","type":"aaaa","value":"2606:2800:220:1:248:1893:25c8:1946"}
{"timestamp":"1506788264","name":"example.com","type":"ns","value":"a.iana-servers.net"}
{"timestamp":"1506788264","name":"example.com","type":"ns","value":"b.iana-servers.net"}
...
Note that the final dataset contains records only for domain names which responded to DNS query. Domain names with NXDOMAIN or SERVFAIL status are not included whatsoever.
What about domain names which refused to respond to ANY query? Good question. These domains are included, however, without meaningful record values as such:
{
"5":"See draft-ietf-dnsop-refuse-any",
"timestamp":"1506672702",
"name":"100.43.157.155.static.krypt.com",
"type":"hinfo",
"value":"ANY obsoleted"
}
Notice type:hinfo. This is usually an indication of ANY query refusal. Although hinfo tells us that domain refused to respond to ANY query, we at least know that domain name is active.
Rapid7 realized this problem and beginning November 2017 started producing separate A and AAAA datasets. What is the difference? Resolution uses A/AAAA query directly instead of ANY query. This way, domains which refused to respond to ANY will now provide valid record value. This dataset, therefore, provides only records with type a or aaaa respectively, whereas regular datasets provide combined records with ns, mx, soa, ...
Forward DNS dataset only includes domain names which were ACTIVE during their resolution.
Reverse DNS study (Rapid7 link)
Similar to its forward DNS counterpart, reverse DNS study provides PTR records collected for the IPv4 address space. PTR records can potentially reveal some hidden subdomains. These subdomains are fed back to the master domain list which is used for Forward DNS study.
DNS usecases
After technical details, here are some practical examples that I use quite often. Snippets assume that you have jq installed and available in PATH. Forward DNS dataset is expected to be saved in a current working directory and named fdns.json.gz. Since the dataset is pretty huge and compressed, expect several minutes for these snippets to finish.
1. Reverse DNS lookup
We can retrieve a list of domain names which some IP address / netrange points to. Note however that we are using Forward DNS dataset since PTR records are usually much less versatile in showing domain names associated with IP address. This is often used to verify whether a particular IP address is hosting multiple virtual hosts.
For single IP address:
zcat fdns.json.gz
| grep -F '<ip_address>'
| jq -r .name
| sort
| uniq
For netrange:
You will need grepcidr.
zcat fdns.json.gz
| grepcidr '<cidr block>'
| jq -r .name
| sort
| uniq
Note that we don't need to parse every JSON to get results. Since IPv4 address is unique to A record, it is sufficient to do grep on raw text and post-process the results.
2. Subdomain enumeration
Subdomain enumeration is one of the essential steps performed during information gathering / reconnaissance phase. It can reveal high-value and forgotten web applications and services that an organization is exposing publicly on the Internet. You can read about subdomain enumeration in my another post. From the more recent tools, I recommend checking amass.
Nevertheless, Forward DNS dataset can also be used for subdomain enumeration (providing very good results):
zcat fdns.json.gz
| grep -F '.example.com"' # double quotes indicate end-of-word
| jq -crM 'if (.name | test("\\.example\\.com$")) then .name else empty end'
| sort
| uniq
Note that we now need to test for correct value by parsing JSON directly. Why? There might be a CNAME record which does include the searched domain name in value field instead of name. This might seem counterintuitive since we are looking for all possible subdomains. In other words, subdomain in value field would be one of them. Notice that we are extracting only name value from the record in the second line. Imagine this example:
{
"timestamp":"1506673702",
"name":"sub.someotherdomain.com",
"type":"a",
"value":"something.example.com"
}
In this case, sub.someotherdomain.com would be included in the result set which is wrong. Alternatively, you can use another approach which removes the need for regex using jq:
zcat fdns.json.gz
| grep -F '.example.com"'
| jq -r .name
| grep '.example.com$'
| sort
| uniq
3. List all IP addresses for domain
Since the cloud is getting more and more prevalent, organizations are slowly moving from dedicated netranges to shared pools of IP addresses owned by a cloud provider. How do we find which cloud providers and IP addresses are some organization using? You guessed it.
In order to find every possible IP address that some subdomain of example.com points to, we can run:
zcat fdns.json.gz
| grep -F '.example.com"' # double quotes indicate end-of-word
| jq -crM 'if (.name | test("\\.example\\.com$")) then . else empty end'
| jq -crM 'if .type == "a" then .value else empty end'
| sort
| uniq
For the sake of simplicity, the snippet only retrieves the IP addresses of subdomains and not example.com itself. You can then use whois against Team Cymru servers to determine a name of ASN to which IP address belongs to:
whois -h whois.cymru.com 8.8.8.8
#AS | IP | AS Name
#15169 | 8.8.8.8 | GOOGLE - Google LLC, US
4. Global DNS analysis
List of a domain can be used to detect malicious domains. One of the latest ideas am I playing around is to using phishing_catcher on Forward DNS dataset.
SSL
Unlike DNS dataset, SSL study provides files in CSV format (without header). SSL study contains full raw certificates as they were observed during SSL handshake. Keep in mind that this is linear IPv4 address space scan and this dataset includes nowhere near all SSL certificates on the Internet. The reason is Server Name Indication (SNI). SNI was introduced to allow multiple separate certificates (not just additional subjectAltName) be present on a single machine. SNI requires specifying domain name upfront, so the server knows which certificate to respond with. Since SSL study doesn't provide domain name with SSL handshake, not all certificates are observed during this scan.
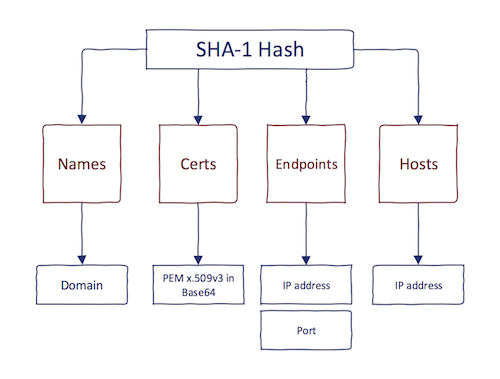
SSL dataset consists of four components. Certificates are hashed using SHA-1, and each of the four components links the hash to different information:
Names
This file has two columns, first being SHA-1 hash and second is Common Name or one of the SubjectAltName entries. It can be used to cluster domain names with the same certificate without parsing each certificate in the first place. These domains are then fed back to the master file for Forward DNS study.
...
2e9b3bac1e5f908f8c4f82cee43024b773be76ac,www-stage.oracle.com
6829d7931876fceceacd6a7a6c6b10c44e03bf59,multicobra.kmgmonitor.khomp.com
57fe089a34678ef36f171bcee2e307d2ef4a3ef4,www.sterowniki.co
c4c81da792367f5b051e053e0aceded4baf83881,2.236.50.21
fce2f73eba30e9f60201b2c34cd1817c957c2432,dev-02.ssrc.org
...
Certificates
This file has two columns, first being SHA-1 hash and second is Base64 encoded x.509v3 in PEM. Note that base64 string is not standardized and most parsers won't work directly. I have created a simple parser for this purpose.
...
952fa955c3daa2c3ca1c78ea07b7c637fa2bb710,MIIFCzCCA/OgAwIBAgIQfHvQ3kjWNNSOns9Uv5d89TANBgkqhkiG9w0BAQsFADByMQswCQYDVQQGEwJVUzELMAkGA1UECBMCVFgxEDAOBgNVBAcTB0hvdXN0b24xFTATBgNVBAoTDGNQYW5lbCwgSW5jLjEtMCsGA1UEAxMkY1BhbmVsLCBJbmMuIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTE4MDMxNjAwMDAwMFoXDTE4MDYxNDIzNTk1OVowFDESMBAGA1UEAxMJZWVpZ2MubmV0MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzi2v5BIO8ZUrWxFLys00QxCqUwN28dQbsMND/QteB5N5amO5S+6PCVzIuOZdDLxZfhbPXqkZ014SyJYZ6hIIkXYLSRIgAqaRUGgGlCAWgpfsVJTQQErGXg6jfTSTjKKIlRi7PQ7Su6hp5ZK8OjxrSwdk4xk7PtHyBBHYch1WtXez9pRFWUrPfs/zIxLEEN2oLqUcOOi03lfKiuvBftz46ACnaWW/tLyRR6kCkU7Wr8H+XeSHCuXHISWmxwgJAfY067ja78+wiDS+3++26k+71vAtOH237LWcz7WSx86Zcyn+sKXTaauBDeL46gepPxL+kpEEPthl3Dcy5qfxvrCNrwIDAQABo4IB+TCCAfUwHwYDVR0jBBgwFoAUfgNaZUFrp34K4bidCOodjh1qx2UwHQYDVR0OBBYEFDrapYAud/y/1sQBWQ+dfbViwswOMA4GA1UdDwEB/wQEAwIFoDAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjBPBgNVHSAESDBGMDoGCysGAQQBsjEBAgI0MCswKQYIKwYBBQUHAgEWHWh0dHBzOi8vc2VjdXJlLmNvbW9kby5jb20vQ1BTMAgGBmeBDAECATBMBgNVHR8ERTBDMEGgP6A9hjtodHRwOi8vY3JsLmNvbW9kb2NhLmNvbS9jUGFuZWxJbmNDZXJ0aWZpY2F0aW9uQXV0aG9yaXR5LmNybDB9BggrBgEFBQcBAQRxMG8wRwYIKwYBBQUHMAKGO2h0dHA6Ly9jcnQuY29tb2RvY2EuY29tL2NQYW5lbEluY0NlcnRpZmljYXRpb25BdXRob3JpdHkuY3J0MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5jb21vZG9jYS5jb20wWAYDVR0RBFEwT4IJZWVpZ2MubmV0ghBjcGFuZWwuZWVpZ2MubmV0gg5tYWlsLmVlaWdjLm5ldIIRd2ViZGlzay5lZWlnYy5uZXSCDXd3dy5lZWlnYy5uZXQwDQYJKoZIhvcNAQELBQADggEBAFy+7GtzcJI+Cg7AdFN2GtaeABJhXCzYtGf688tMDwe0LqJLmQQwoltJ2GUStT44LSwq3h/JdKndNSD9r6Dn0wQpQsFBjW+hNRBvwg0f3Mpm7uRbtyHKHgnn8QIuFtb6xD9Poohx80AVPrYaydtG+J4MNPyf0++83Xjvzf0OKoiGkK9TLexuilV8KbxxJ2WVRrO2OCZPhQ1lr46dokxnZYNXzXk9Qn+PaRlnM6riaOy999QBf9u6/Py50x5LORNlTxt9k+GqUP3laPOe6NGQ/aiTm0ghyCJ5dg8iENdFCUSF1x6a1OoeRJNL7bKf/JH15Mtk0K9tVEdwXKBSp2sytZU=
454c679ffac21843648cd103fc46f4cc3205d7d8,MIIGBjCCBO6gAwIBAgIQAppCMvPnnfBNj0/St+NnSDANBgkqhkiG9w0BAQsFADBNMQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMScwJQYDVQQDEx5EaWdpQ2VydCBTSEEyIFNlY3VyZSBTZXJ2ZXIgQ0EwHhcNMTgwMzE0MDAwMDAwWhcNMTkwMzE0MTIwMDAwWjBVMQswCQYDVQQGEwJJVDESMBAGA1UEBxMJU2NhbmRpY2NpMRwwGgYDVQQKExNHdWNjaW8gR3VjY2kgUy5wLkEuMRQwEgYDVQQDDAsqLmd1Y2NpLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAJe+s1rVtphcSzTbUexc5vVlxMYTrMj7S/u8YCZDqZrO1OwYAvnDj4zKz6OVqg561Xh8MDMOaXzxfi3A5RNa1oEQPSBcJedCb/Pbk8rF0uhjAvf5iAhZTanJJQKY/2JBlaJECMTI3e3nvIT+CROkhxJthc0vpEkAieeT8fzMqX8tvVVrBINieogZNud8cUr03qeht3j2OJaJHu5P2v5/+pNg1bMuvLlky9Qtr5vg5/xKwakUbMguv+aFaCyeBZ6EQOny83G0eMUfu8i544O8WiwqHoWfl0Ue1SJZV84L0QC4OWLXvun+oKSXbLC86NuQ1PZPkpkQTUh30ASnP7u5lJsCAwEAAaOCAtgwggLUMB8GA1UdIwQYMBaAFA+AYRyCMWHVLyjnjUY4tCzhxtniMB0GA1UdDgQWBBTXNBv/6Vl7d1w59/Nq5x1/VyQ7qjAWBgNVHREEDzANggsqLmd1Y2NpLmNvbTAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMGsGA1UdHwRkMGIwL6AtoCuGKWh0dHA6Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9zc2NhLXNoYTItZzYuY3JsMC+gLaArhilodHRwOi8vY3JsNC5kaWdpY2VydC5jb20vc3NjYS1zaGEyLWc2LmNybDBMBgNVHSAERTBDMDcGCWCGSAGG/WwBATAqMCgGCCsGAQUFBwIBFhxodHRwczovL3d3dy5kaWdpY2VydC5jb20vQ1BTMAgGBmeBDAECAjB8BggrBgEFBQcBAQRwMG4wJAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBGBggrBgEFBQcwAoY6aHR0cDovL2NhY2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0U0hBMlNlY3VyZVNlcnZlckNBLmNydDAJBgNVHRMEAjAAMIIBBQYKKwYBBAHWeQIEAgSB9gSB8wDxAHcApLkJkLQYWBSHuxOizGdwCjw1mAT5G9+443fNDsgN3BAAAAFiJTegOgAABAMASDBGAiEAg9aSzszLwa0R+2QqUXnbkh7V31LlkloOOlal9MyfjlACIQDcMT1dxGzuGwXq4Osh6vQ9xK+5bo3S5k8O5sE8BmPEagB2AG9Tdqwx8DEZ2JkApFEV/3cVHBHZAsEAKQaNsgiaN9kTAAABYiU3oaMAAAQDAEcwRQIgRD2deJbn56dV/8Gr1jwVQ+WprCqS6+D2umM8HeU3Ar0CIQCxHmoSpvhnTNUUX6ZzR6sqhvYV4849jBZ3mMKofap3DjANBgkqhkiG9w0BAQsFAAOCAQEAiYVGJso56v1qqIT5Id9ALdSsS+rB0+t0/IiAH3XXiDprPhjXtpyyMssitGUJWqDTRYfptjdi5z7U9dv5vZARZv9AwLuzgvwLQ3G0DGV3qQj//DCS+TwWC3voSsq6pyP3ZkTHcqAKQqXOpuaiG1caHvG6JBAGv0QPMGBvn2ckQf8v5DphbUiy8jidUy1REUwY9nOqy/i+HF0dS4sHxINnqbwzYkoqjJ7UkVd6faRknhodTsfEGJFhYkWoQlCRVPBCME9plKedWLFssfCjnuomxVCKV3aXOIYSR5hYwPDs+tbuk1hQm1zLW5hRFhZ3xanCY/HvT/2t7zyKeq7wFe8vFg==
a08f3182c5c1f8768b1bb42d3d262614d13568dc,MIIFvzCCBKegAwIBAgISAx0bHcSRqeZbpaUEgOfs7ZbnMA0GCSqGSIb3DQEBCwUAMEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQDExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xODAzMTQyMjUyNTNaFw0xODA2MTIyMjUyNTNaMBwxGjAYBgNVBAMTEXd3dy53aG9maW5hbmNlLmRlMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAxrwWcS/D1ITZRjlKaugi3hSuuEljlRBbYzEQD0nw15lnbEqbD+EMgOB1hFMvif4QQZMj55ccbp0K78TvWkemPQGnnrVHUbhoixeAiDf5Ib69u9a3xjrMDlrxT8lggOKsC5RGxPtK8tLIPBOuz9F6REseAwSMN9lk5VifrRmm76zOeVo7BN8mD2fG07f3WxW0O+6FvWP/bFQ2pMH0DYeb5CdRGfWfDAKEl4qB8M8sWOTjAr/3YS1mTWQNn8RKbjZ1VGzj8yJn6F5uVWDCMg9wuAOTras2wWeJocFzwvxbFif0i3LbgRbyObPUY/EQuflPjxK+jfK5oOhSB9FGB1zuKQIDAQABo4ICyzCCAscwDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBRV2EzKmgW/j2iniIQa94uZ0ap2UDAfBgNVHSMEGDAWgBSoSmpjBH3duubRObemRWXv86jsoTBvBggrBgEFBQcBAQRjMGEwLgYIKwYBBQUHMAGGImh0dHA6Ly9vY3NwLmludC14My5sZXRzZW5jcnlwdC5vcmcwLwYIKwYBBQUHMAKGI2h0dHA6Ly9jZXJ0LmludC14My5sZXRzZW5jcnlwdC5vcmcvMIHVBgNVHREEgc0wgcqCE2FkbWluLndob2ZpbmFuY2UuZGWCFGFkbWluMi53aG9maW5hbmNlLmRlghFhcGkud2hvZmluYW5jZS5kZYITYXBwMDMud2hvZmluYW5jZS5kZYISYmxvZy53aG9maW5hbmNlLmRlghJuZXdzLndob2ZpbmFuY2UuZGWCFHNlY3VyZS53aG9maW5hbmNlLmRlghVzaXRlbWFwLndob2ZpbmFuY2UuZGWCDXdob2ZpbmFuY2UuZGWCEXd3dy53aG9maW5hbmNlLmRlMIH+BgNVHSAEgfYwgfMwCAYGZ4EMAQIBMIHmBgsrBgEEAYLfEwEBATCB1jAmBggrBgEFBQcCARYaaHR0cDovL2Nwcy5sZXRzZW5jcnlwdC5vcmcwgasGCCsGAQUFBwICMIGeDIGbVGhpcyBDZXJ0aWZpY2F0ZSBtYXkgb25seSBiZSByZWxpZWQgdXBvbiBieSBSZWx5aW5nIFBhcnRpZXMgYW5kIG9ubHkgaW4gYWNjb3JkYW5jZSB3aXRoIHRoZSBDZXJ0aWZpY2F0ZSBQb2xpY3kgZm91bmQgYXQgaHR0cHM6Ly9sZXRzZW5jcnlwdC5vcmcvcmVwb3NpdG9yeS8wDQYJKoZIhvcNAQELBQADggEBACuzEMZ006I8O/nrZ2zVslhCbrhZxDsjoU1loKxKsOW0dhLoXTRKHaCvL56t0Bj3JuSVIuipqsSWy+9JPwfQa3m4YprEsi3e/iyeEq3fnJFq9mnQi4iJAl35dZCYCyIzNxg7fUP8JMpoByDupCSjfKQMwaSivsW7V+UJJBc/EYPmq69UG7l8YRHKPQ+GHFn/dsGY080jQJ/UddJS/y2UGrAMh8wtsdS769WylZSBD4U8AhRW/rE+5dsrfLcSCzgBZtqBIJW7Lb2C8F8uv3axqS7IY5fecYjxbGSTovGG4iCaIw56sEsseeRGSaEwL531IanQzrfIClQ9VQRp05UBMpg=
...
Hosts
This file has two columns, first being IP address and second an SHA-1 hash of certificate that was observed on the IP address.
...
104.17.240.209,23514bc3102129ec1937110222f66325afa239de
66.175.219.116,18ac236c460e931de0946e77721577ae2640b69a
216.104.176.126,c86edbc71ab05078f61acdf3d8dc5db61eb75fb6
67.222.48.198,184f0bdec1ce4356d50db75c2dbd6a4f5ae299a4
72.1.240.148,0c9fea8c07b9a3b47d1b2c076fda31248b83e404
66.228.51.132,eab040689a0d805b5d6fd654fc168cff00b78be3
...
Endpoints
This file has three columns, first being an IP address, second is port, and third is an SHA-1 hash of certificate that was observed on the IP address. As you can see, this is very similar to the Hosts file.
...
104.17.240.209,443,23514bc3102129ec1937110222f66325afa239de
66.175.219.116,443,18ac236c460e931de0946e77721577ae2640b69a
216.104.176.126,443,c86edbc71ab05078f61acdf3d8dc5db61eb75fb6
67.222.48.198,443,184f0bdec1ce4356d50db75c2dbd6a4f5ae299a4
72.1.240.148,443,0c9fea8c07b9a3b47d1b2c076fda31248b83e404
66.228.51.132,443,eab040689a0d805b5d6fd654fc168cff00b78be3
...
In some SSL dataset, I noticed that even SHA-1 of the certificate is present in the Hosts file, it is missing in Certificates file.
Project Sonar provides other studies such as:
- HTTP — HTTP responses for full IPv4 address space. Note however that this is scan based on IP addresses. VHosts are not taken into account, so the final dataset is heavily limited by it. Links in returned HTML are used to feed the master list for Forward DNS study.
- HTTPS — Similar to one above, but for HTTPS.
- More SSL certificates — Similar to SSL study, but this dataset contains certificates for POP, SMTP, ...
- TCP scans — Similar to Censys TCP scans across IPv4 address space.
- UDP scans — Similar to Censys UDP scans across IPv4 address space.
Until next time!

