In this post, continuing with OSINT related topics, we will look at researching people. Similarly to domains, there are some specific goals during our "person analysis":
- The person is our new acquaintance. We want to find some information about him/her.
- You want to hire a new employee. Besides standard background check by HR, you might want to perform your OSINT to see, whether he/she will be a good candidate.
- You want to pitch a new business product to a high-profile individual in some particular company. You need to get his/her e-mail or mobile number first. Note that this step usually includes some organizational research which will be cover in next parts of this series.
- You are a penetration tester and are currently doing spear phishing assessment. You need to find information to increase the potential success of the phishing assessment.
As you can see, there are multiple situations where OSINT about people might come in handy. Let's look at some specific techniques.
Note: The techniques in this guide should NOT be used for malicious purposes. Although it is hard to write a guide without the methods that can be used in malicious scenarios, I am not responsible for such actions.
OPSEC
Before we begin, I want to mention something important. You may have heard about operational security or OPSEC. During the searches, you might expose yourself in many different ways. For example, if you are logged in to LinkedIn and visit some other profile, the person will be notified about that (including your name). OPSEC can be thus seen as guidelines in a specific context. These guidelines prevent the other person from knowing either that the OSINT is being performed on them or knowing YOUR true identity.
I recommend using Tor Browser Bundle for all OSINT related activities. Firstly, your IP identity is hidden because of several encrypted connections a.k.a onion. Secondly, the customized version of Firefox assures that between the restarts, the cookies are deleted, and so no past activities can be fingerprinted. You should never login to your accounts using Tor.
If the speed of Tor is problematic to you, you can opt to use VPN service combined with some safe browsing environment. Again, you don't want to expose the cookies in any way. The simplest option is to use Private Mode in a browser, although I would go as far and recommend using virtual machine dedicated to OSINT.
Social Media
First thing I like to do is to find the social media profiles. Why? I believe that they hold the majority of useful OSINT information. You should expect multiple false positives when dealing with popular names such as John Smith, etc.
Finding social media profiles might be difficult or easy depending on privacy and consistency of your target. Simple Google search will sometimes do its trick:
John Doe site:facebook.com
John Doe site:instagram.com
John Doe site:linkedin.com
...
Note that for several social media sites, you will need to have an account created to see the full profile. I recommend creating a fake account for this purpose.
People tend to reuse their usernames across different services. Username there acts as a unique identifier of a person across the Internet. I like to extract the username from the Instagram of the person. Then, I use a service called namechk to search for this username across many different social media platforms.
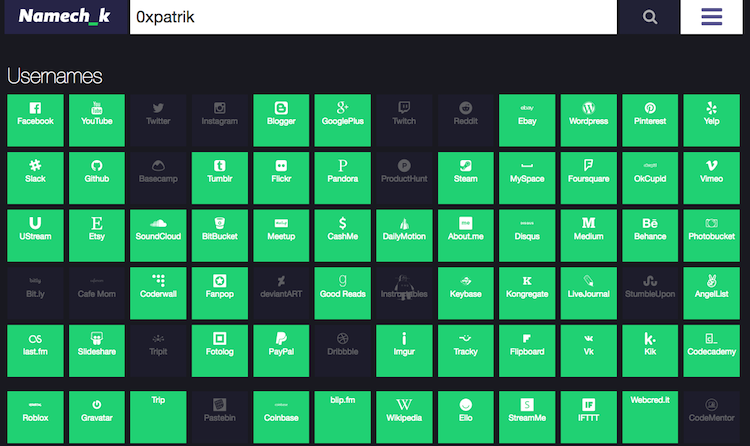
I have to say that I haven't registered an account on all of the indicated platforms. You should expect some false positives, as always.
There are also aggregator such as pipl.com or social-searcher. Although I don't always use them, they tend to provide a more high-level view of the person.
Prospects
This is a topic that can be suited both here and to organizational OSINT as well. I decided to stick it here since I think it mostly relates to people than organizations itself.
When dealing with sales, it is often necessary to have a good contact in the organization to pitch to. You should be smart about that and decide, which person is the right choice. Certainly, it is not a good idea to pitch an infosec related product to CEO of Fortune 500 company. CISO or Senior Security Engineer might be a better choice here. On the other hand, pitching a security-related product to CEO of startup makes more sense.
I don't want to describe the full cold calling/e-mailing approach here; I want to explain the best ways to find the contact information of key people in your target organization. I highly recommend checking Clearbit Prospector for this task. It is a great product with accurate data. Although it is a paid product, I honestly think it is worth the money if you are doing lot of such searches. Yes, it is not OSINT in a true sense, other techniques are explained below.
Another product that I like is Hunter.io. Again it is a paid product, but you have a 100 searches / month for free. Similar services are called voilanorbert and headreach. They also operate on a freemium model. I think that this is the best way of finding e-mail addresses for specific people in organizations.
Alternatively, you can use LinkedIn for the initial cold message. You simply use Search bar with query <COMPANY_NAME> <POSITION> and get the most accurate results. People tend to keep their LinkedIn profiles updated. You can then connect with them easily (although not via e-mail). A similar thing applies to Twitter. However, I would say it is a less formal medium.
Pro tip: For smaller companies, the e-mails are usually listed directly on their website.
For some useful Google Dorks about cold calling, I recommend this article.
Telephone Numbers
Finding telephone numbers is more tricky than e-mails. My go-to tool is either Google where I try to dork using the name of the person and some combination of telephone number keywords or use White/Yellow Pages in the particular country such as whitepages.com for the US. Make sure to check awesome-osint for a list of telephone number searching services.
Sometimes, I need to perform a reverse telephone search: Given the telephone number, I want to retrieve the name of its owner. This is useful when you have missed calls which you want to correlate to the owner. You could either use services described above, but the more universal approach is as follows:
- Try the Facebook search with the number. The owner should come up in the results if he/she has the number associated with the profile.
- Save the number in your phone and look at Viber or WhatsApp contact list. These services allow specifying photo and the name of the owner and this information can be extracted just by knowing the telephone number.
E-mails
I described finding e-mails in the Prospecting section above. Now, I want to extend that and talk about more technical things about e-mail OSINT. SMTP support two, not very well-known commands VRFY and EXPN. The former is used to verify directly on the mail server, whether some particular mailbox exists or not. This is particularly useful when you are already familiar with standard e-mail address format for the company. The formats are usually:
lastname@company.tld
firstname.lastname@company.tld
firstletterfirstname.lastname@company.tld
The easiest way to test this is to use an online tool such as MailTester.com. Don't be distracted by a historic design of this websites. It does the outstanding job compared to other similar services. Note that not every SMTP server allows this command (apparently), but from experience, even the high-profile organizations sometimes have this turned on (ehm, Apple).
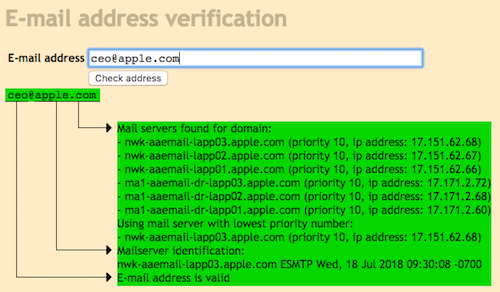
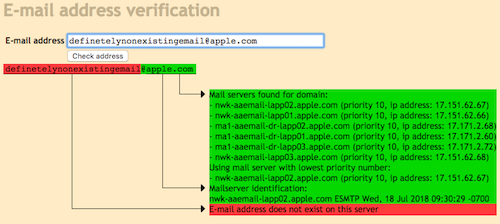
The EXPN command is used to list members of some distribution list. SMTP server provides the individual e-mail addresses of such members.
I also like to test, whether some e-mail address is present in some dump of leaked credentials. The easiest way is to use Have I Been Pwned by Troy Hunt. This is useful in combination with security assessment. Why? Usually, people reuse passwords, and there is a chance that the password that user used in some services from which the credentials were stolen is used in a corporate environment as well.
The purpose of this guide is not to flood you with as many tools as possible. Rather, I try to explain different techniques. If you want to use different tools, you can find the right one here. Note that some of the tools work only in specific countries.
Parts in this series:
OSINT Primer: Domains
OSINT Primer: People
OSINT Primer: Organizations
Until next time!

